- Over 30,000 websites get hacked every single day.
- WordPress powers 43% of the internet, which makes it the biggest target.
- And 43% of cyberattacks target small businesses, not just big brands.
Why WordPress Sites Get Hacked
Weak Passwords

Most hacks start with something simple: stolen or weak passwords.
Passwords like password123, admin2025, or your pet’s name are child’s play for hackers. Automated bots can guess thousands of combinations every second until they break in.
How to fix it:
Outdated WordPress, Themes, or Plugins
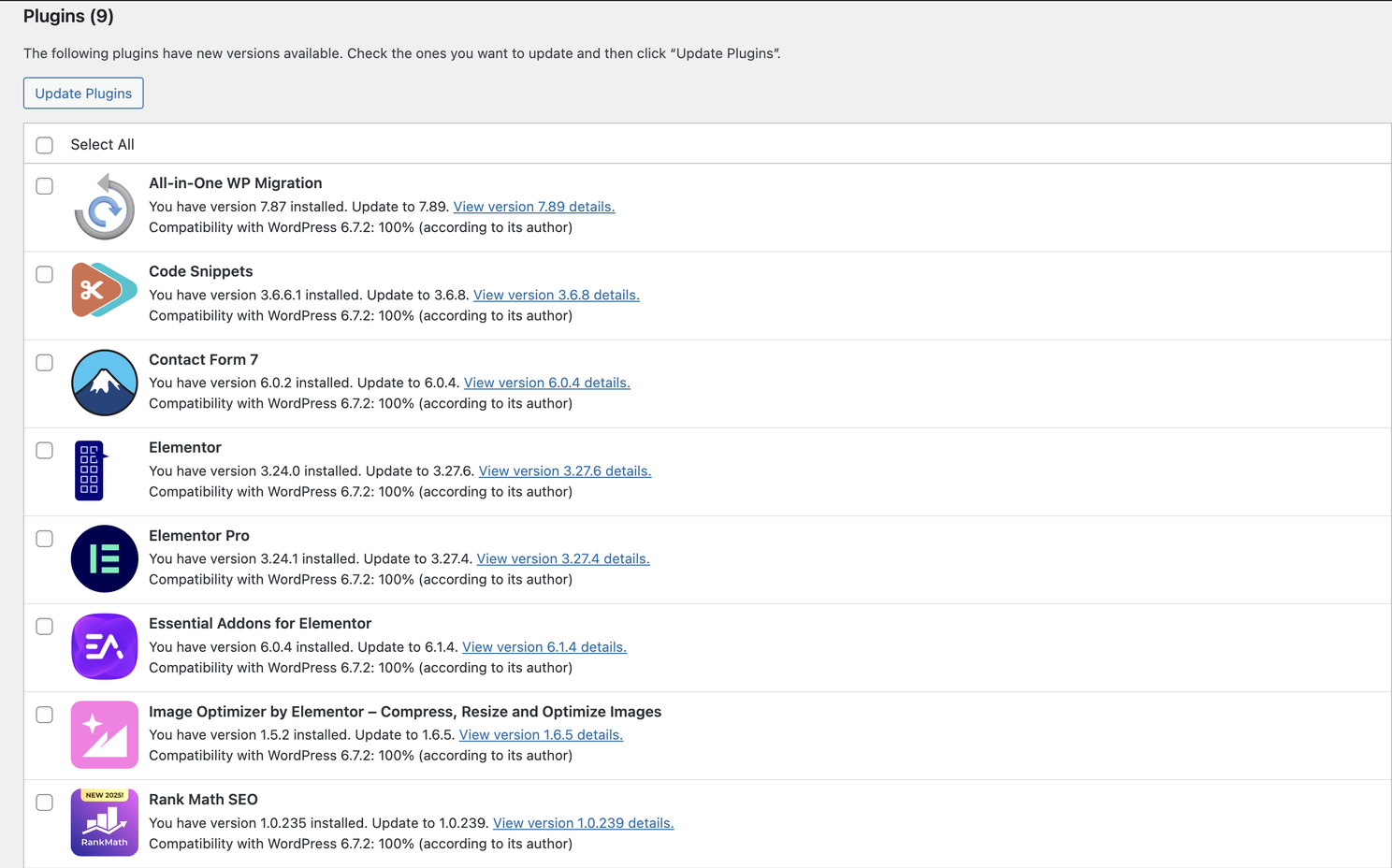
How to fix it:
- Update WordPress core, plugins, and themes weekly.
- Delete unused plugins and themes instead of letting them sit idle.
- Only install tools from trusted sources that are actively maintained.
Cheap or Weak Hosting
How to fix it:
- Use a security-focused host like Kinsta, WP Engine, or SiteGround.
- Enable server-level firewalls and DDoS protection.
- Make sure your host offers automatic daily backups.
Good hosting is not just about security, it also prepares your site to handle big traffic spikes without crashing. If you are planning a product launch, a sale, or expecting a sudden surge of visitors, you’ll want to be ready. We wrote a step by step guide on how to prepare your WordPress site for a high traffic event so you can stay online even when the pressure is on.
No SSL Certificate
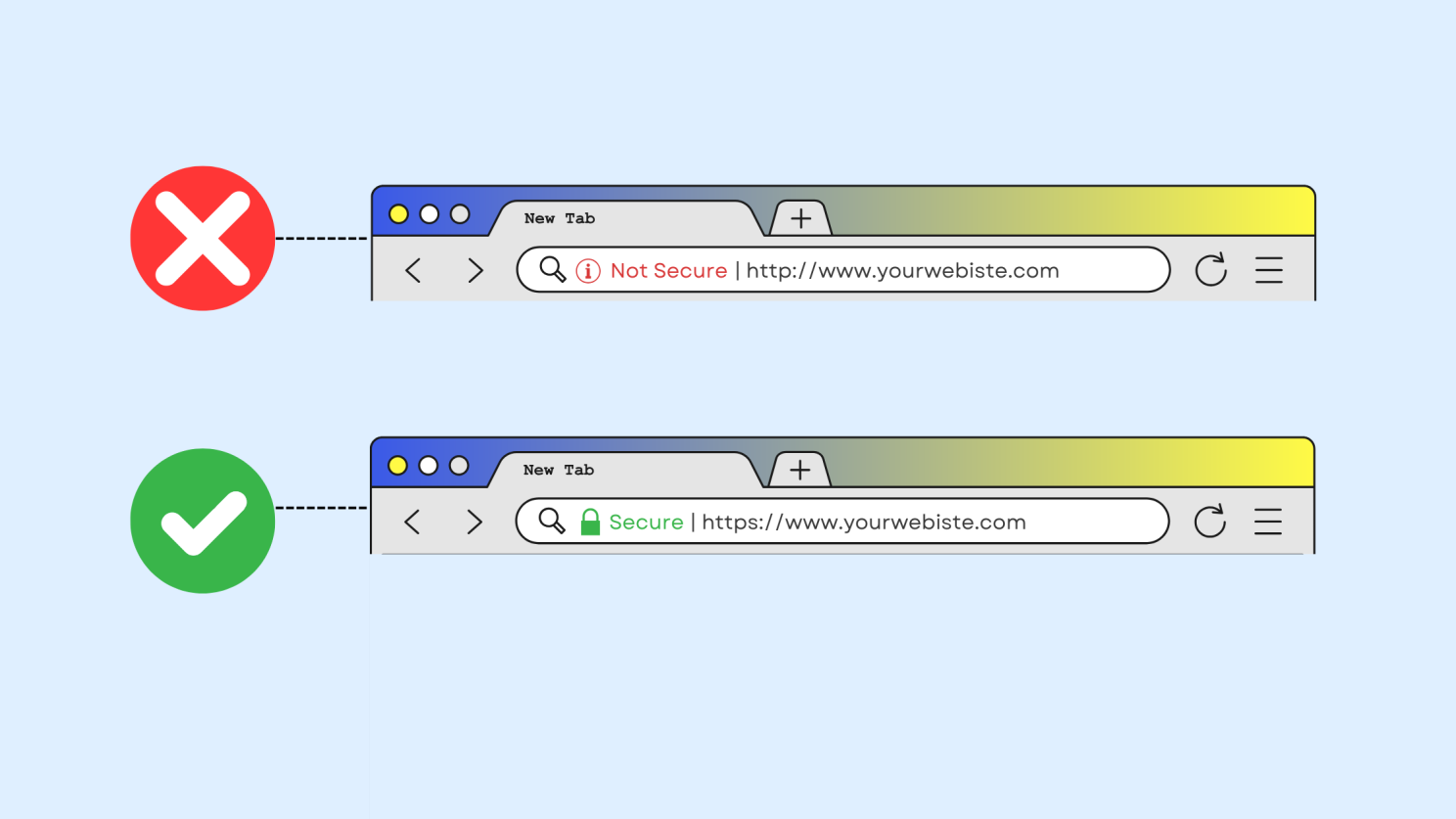
If your website still shows “Not Secure” in browsers, you are putting both your visitors and your business at risk. Without SSL, all data (logins, payments, emails) is sent in plain text, which hackers can easily steal. Worse, a missing SSL can instantly damage trust. Studies show poor security can cost you up to 30% of your customers.
How to fix it:
- Get an SSL certificate. Most hosts provide free Let’s Encrypt SSLs.
- Force HTTPS on every page using a plugin like Really Simple SSL.
- Update your internal links to HTTPS to avoid mixed-content issues.
No Security Plugin

How to fix it:
- Wordfence: real-time firewall and malware scanner.
- Sucuri: cloud-based monitoring and protection.
- Solid Security: easy setup with strong defaults.
These tools block brute force attacks, scan for malware, and alert you before damage is done. If you want to see what else your site needs beyond security, take a look at our guide on the 7 best WordPress plugins you should install first. It will help you set up your site the right way from the very beginning.
Pirated Themes and Plugins

How to fix it:
- Always buy from trusted vendors like ThemeForest or the official WordPress repository.
- Never install pirated (“nulled”) software. The cost of fixing a hacked site is far higher than buying the real thing.
Using Plain FTP Instead of SFTP/SSH – A Hacker’s Dream Come True
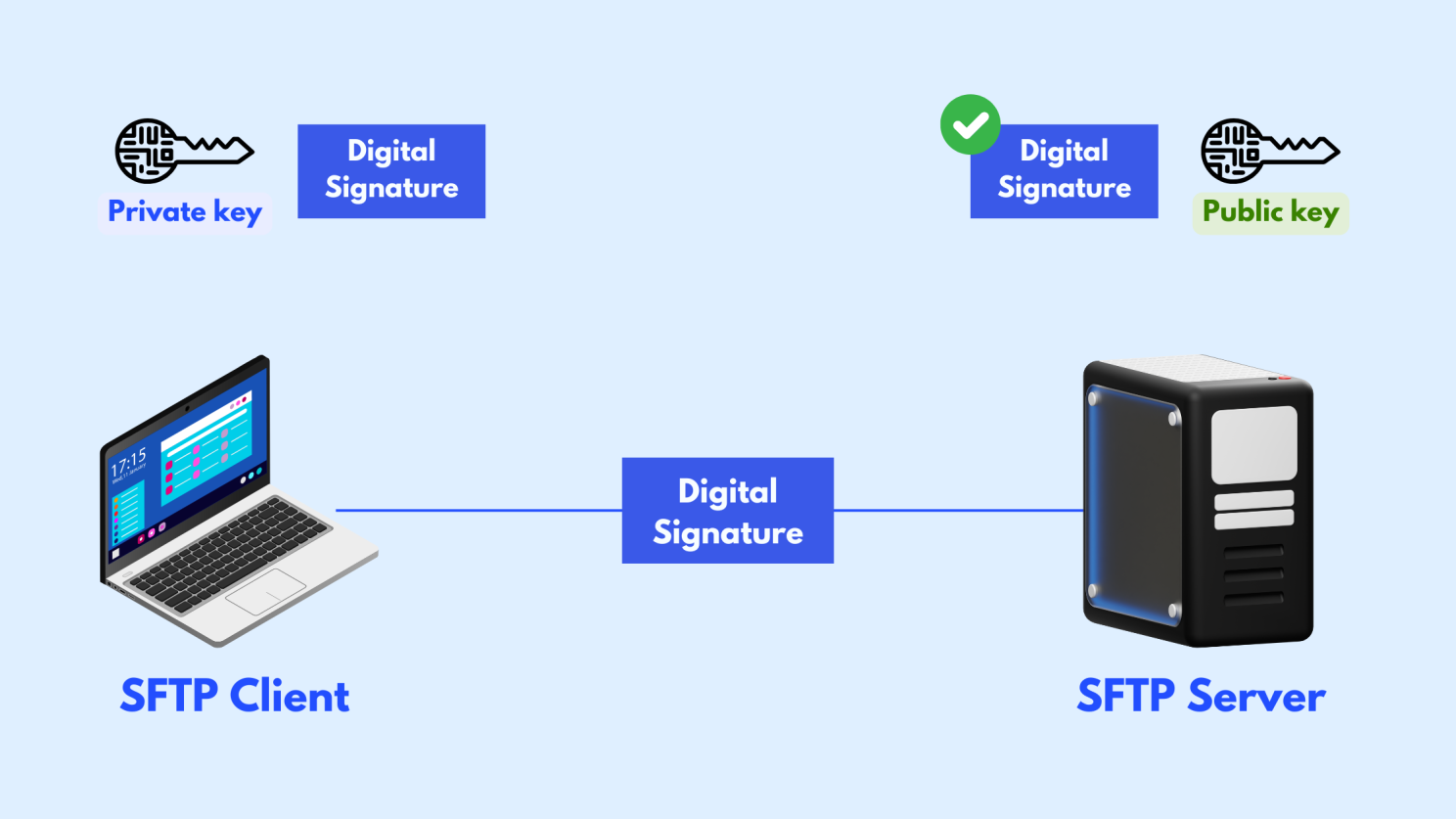
Why FTP is a Huge Security Risk
- FTP sends usernames and passwords in plain text, which means anyone monitoring the network can intercept them.
- Hackers can use packet sniffing tools to capture your login details within seconds on an unsecured connection.
- Once they have access, they can modify your files, delete your website, inject malware, or steal customer data.
How to Fix It and Make File Transfers Secure
- Use SFTP Instead of FTP: SFTP (Secure File Transfer Protocol) encrypts your login credentials so they cannot be intercepted.
- Disable Plain FTP on Your Server: Most modern hosting providers allow you to block FTP entirely and enforce secure connections.
- Switch to SSH for Server Access: If you need command-line access, SSH (Secure Shell) is a much safer alternative to Telnet or FTP.
- Use Strong Passwords or SSH Keys: Where supported, set up SSH key authentication instead of relying solely on passwords.
Example: A web designer used plain FTP to upload client sites. One day, hackers intercepted their credentials, infected 15 client websites with malware, and caused a Google blacklist nightmare. After switching to SFTP, the issue never happened again.
Lesson: If you wouldn’t send your credit card details over email, don’t use FTP. Use SFTP or SSH and keep your site secure.
Default WordPress Database Prefix: An Easy Target for Hackers
Why the Default "wp_" Prefix is Dangerous
- SQL Injection Attacks: Automated scripts inject malicious SQL commands into your database. Predictable table names make this process effortless.
- Data Theft: Attackers can directly target the wp_users table to steal admin credentials.
- Website Defacement: Rogue code can be injected into wp_posts or wp_options to manipulate or take over your site.
How to Fix It by Changing the Database Prefix
- Change the Prefix During Installation: When setting up WordPress, change the default prefix from wp_ to something unique like site123_ or mywp_.
- Change the Prefix on an Existing Site: If your site is already live, you can still make changes. Use a security plugin such as Solid Security or WP-Optimize to safely update your database prefix. If you are confident with technical work, you can also manually edit the wp-config.php file and rename tables in phpMyAdmin.
Example: A WordPress agency reviewed ten hacked sites. Eight of them were using the default wp_ prefix, and all had been hit by SQL injection attacks. After changing the prefixes to unique ones and strengthening their overall security, the attacks stopped.
Lesson: Hackers love defaults because they make their job easier. Do not give them the advantage. Change your WordPress database prefix to something unique and add an extra layer of protection to your site.
Not Limiting Login Attempts: Leaving Your Front Door Wide Open
Why Unlimited Login Attempts Are a Major Risk
- Brute Force Attacks: Bots test thousands of passwords every second until one works.
- No Limits Mean Easy Targets: If your site does not restrict failed login attempts, hackers can keep trying indefinitely.
- WordPress Default Settings: By default, WordPress does not include login attempt restrictions, leaving your site exposed.
How to Protect Your Login Page
- Install a Login Limiting Plugin: Use a plugin such as Limit Login Attempts Reloaded. It blocks suspicious IPs after repeated failures. You can set rules such as locking out a user after three failed attempts for 30 minutes.
- Enable IP Banning: Block IP addresses that repeatedly attempt failed logins to prevent them from returning.
- Add Two-Factor Authentication (2FA): Even if someone guesses your password, 2FA requires a second verification step, such as a code from your phone, which makes unauthorized access nearly impossible.
- Change the Default Login URL: Hackers know the standard WordPress login URLs (/wp-admin or /wp-login.php). Change yours using a plugin like WPS Hide Login to make it harder for bots to find.
Example: A WooCommerce store faced more than 1,000 failed login attempts every day. After installing a login limiting plugin, enabling two-factor authentication, and changing the default login URL, brute force attacks dropped to almost zero.
Lesson: Unlimited login attempts are an open invitation to hackers. By setting limits, enabling 2FA, and hiding your login URL, you significantly reduce the risk of brute force attacks and keep your site secure.
Securing wp-config.php — Your Most Important File
Why wp-config.php is a Prime Target
- Database Credentials: If hackers obtain your wp-config.php file, they immediately have your database username and password, giving them full access to your content.
- Browser Access: Without protection, wp-config.php can sometimes be viewed directly in a browser, exposing sensitive details.
- Malware Injection: Attackers often modify this file to add hidden code that steals data, redirects users, or creates secret admin accounts.
Why wp-config.php is a Prime Target
Step 1: Move wp-config.php Outside the Public Directory
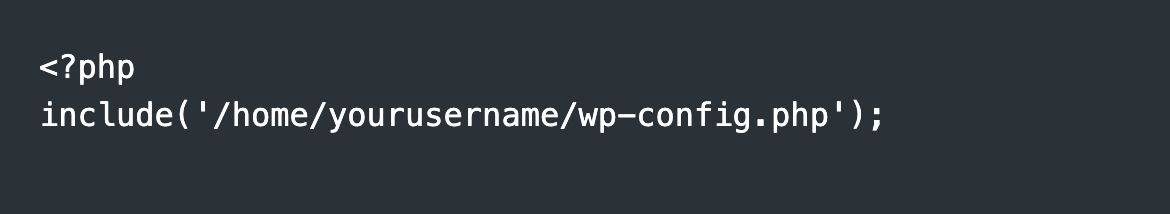
Step 2: Restrict Access with .htaccess

Step 3: Set Correct File Permissions
File permissions determine who can read or edit your files. For wp-config.php, you should restrict access so that only you (the site owner) can read it, and no one else — not even other scripts — can modify it.
Key Takeaway
Weak File Permissions — Leaving Your Website Exposed

Why Weak File Permissions Are a Security Risk
- Hackers Can Upload Malicious Files: Loose permissions allow attackers to place hidden scripts inside your server. These scripts can steal sensitive information, create backdoors for future access, or inject malware.
- Core Files Can Be Modified: WordPress relies on essential files to function correctly. If hackers gain the ability to alter or delete them, they can break your site or replace files with malicious code.
- Risk of Hosting Suspension: Many hosting providers monitor sites for malware. If your site is compromised due to poor permissions, they may suspend it to prevent the infection from spreading to other websites on the server.
- The Common Mistake of Setting 777 Permissions: Some site owners mistakenly set all file permissions to 777 (full access for everyone) in an attempt to “fix” issues. This gives hackers unrestricted control and is one of the most dangerous misconfigurations.
How to Check and Correct Permissions
- Log in to your hosting control panel (such as cPanel or Plesk) or connect via an FTP client like FileZilla.
- Navigate to the WordPress root directory, typically named public_html/.
- Right-click on any file or folder and choose File Permissions or Change Permissions.
- Apply secure settings:
Folders: 755
Files: 644
Key Takeaway
Keeping XML-RPC Enabled — The Hidden Backdoor for Hackers
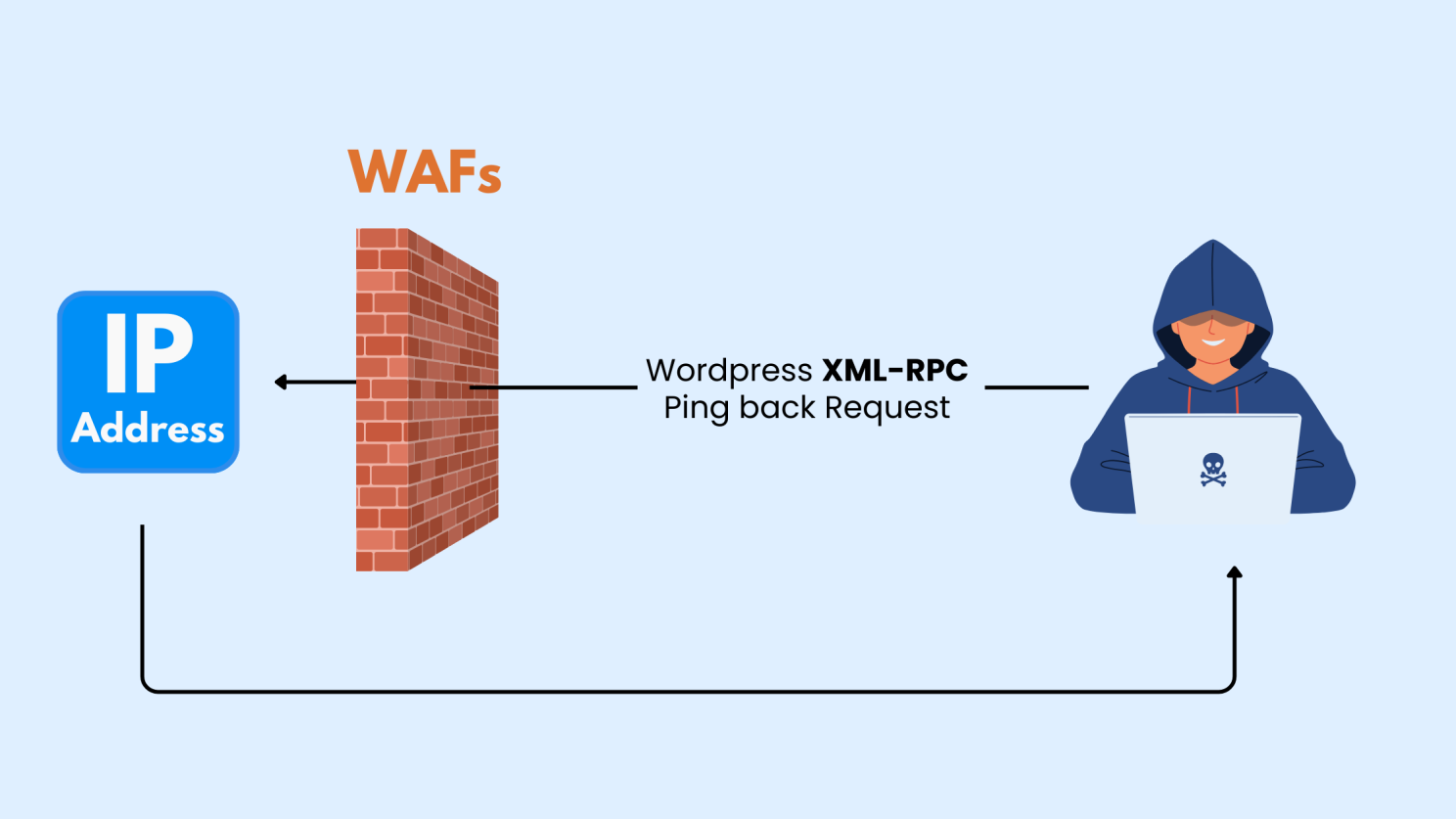
What is XML-RPC?
Why XML-RPC Creates Security Risks
- Brute Force Attacks Become Easier: Hackers can use XML-RPC to attempt thousands of password combinations in a single request, making brute force attacks far more efficient.
- Potential for DDoS Attacks: Attackers can exploit XML-RPC to send massive volumes of requests to your server, overwhelming it and causing downtime.
- It Is Rarely Needed Today: Most plugins and APIs no longer depend on XML-RPC. Keeping it enabled only increases your exposure to risk without offering much benefit.
How to Disable XML-RPC and Secure Your Site
- Use a PluginThe simplest method is to install a plugin such as Disable XML-RPC. This blocks all access to the file instantly.
- Block Access via .htaccessIf you prefer a manual solution, add this code to your .htaccess file in the root directory of your WordPress site:

This prevents direct access to the XML-RPC file.
- Use a Security PluginComprehensive security plugins like Wordfence and Sucuri automatically monitor and block XML-RPC based attacks as part of their firewall protection.
Not Setting Up a Web Application Firewall (WAF) — Leaving Your Site Unprotected

Why a WAF Is Essential for WordPress Security
- Hackers Exploit Vulnerabilities Instantly: When new security flaws are discovered in plugins, themes, or WordPress itself, hackers often begin exploiting them within hours. A WAF blocks these attempts in real time, buying you critical time to update your software.
- Defense Against SQL Injection and Malware: Hackers frequently try to insert malicious code into form fields, search bars, or URLs. A WAF inspects this traffic and blocks these injection attempts before they reach your site, preventing stolen data or corrupted files.
- Protection Against Bots and Automated Attacks: Attackers rarely act manually. They use automated bots to hammer login pages, scrape data, or flood servers. A WAF filters this traffic so your site remains stable and your server resources are not wasted.
- First Line of Defense Against DDoS Attacks: A Distributed Denial of Service (DDoS) attack overwhelms your server with fake traffic until your site crashes. Many modern WAFs automatically detect unusual traffic patterns and stop the attack before it disrupts your business.
How to Protect Your Site with a WAF
- Install a Web Application Firewall: Use trusted services like Cloudflare, Sucuri, or Wordfence. These platforms monitor every request to your site, filtering out malicious traffic before it does any damage.
- Enable Bot Filtering: Many WAFs allow you to identify and block bad bots that attempt brute-force logins, spam form submissions, or aggressive scraping. This reduces server strain and keeps your website accessible to genuine visitors.
- Activate DDoS Protection: If your site is a target for high-volume traffic attacks, enable DDoS protection. Premium services like Cloudflare Pro can automatically detect and neutralize large-scale attacks, ensuring your site stays online.
Conclusion
At Launchwithwp, we build WordPress sites that are fast, secure, and reliable from day one. Our dedicated security service adds firewalls, malware protection, and ongoing monitoring so your site stays safe while you focus on growing your business.
👉 Protect your WordPress site with Launchwithwp today.


